
If you’ve ever wondered about the mysterious file named xmlrpc.php that resides within your WordPress website, you’re not alone. xmlrpc.php might sound complex, but XML-RPC in WordPress plays a crucial role in enabling communication and interaction between your WordPress site and other external systems or applications.
XML-RPC is a vital component of the WordPress framework that often goes unnoticed by many website owners and bloggers.
In simple terms, XML-RPC is a remote communication protocol in WordPress that enables external systems and applications to interact with your website. It allows you to perform various actions such as creating posts, managing comments, and retrieving site information remotely. While XML-RPC offers convenience, it can also pose security risks if not properly managed.
In this article, we will learn about XML-RPC in WordPress, its functionality, and the importance of disabling it for enhanced security. We will also explore the methods to disable XML-RPC and safeguard your WordPress website from potential vulnerabilities. So, let’s dive in and discover the world of XML-RPC in WordPress and how you can effectively manage it.
Table of Contents
What is XML-RPC in WordPress?
XML-RPC is a remote communication protocol that enables data exchange between different systems over the internet. It stands for Extensible Markup Language Remote Procedure Call. XML-RPC serves as a bridge between different platforms, allowing them to interact and share information seamlessly.
At its core, XML-RPC relies on XML (Extensible Markup Language) as its data format. XML provides a standardized way of structuring and representing data, making it easily understandable and interpretable by various systems. With XML-RPC, data is encoded in XML format and transmitted between a client (requesting system) and a server (responding system) using HTTP as the transport protocol.
The purpose of XML-RPC is to facilitate remote procedure calls (RPC) between systems. It allows a client to invoke methods or functions on a remote server and receive the results back. These methods can be part of the server’s own functionality or provided by plugins, extensions, or APIs.
XML-RPC has played a significant role in the WordPress ecosystem. It has enabled remote management and interaction with WordPress sites, offering functionalities like remote publishing, content syndication, comment management, and trackbacks/pingbacks. By utilizing XML-RPC, users can perform these operations without directly accessing the WordPress admin dashboard, making it a convenient and flexible solution.
Is XML-RPC in WordPress a Security Problem?
However, XML-RPC in WordPress has also faced security challenges over the years. It has been a target for brute-force attacks, where malicious actors attempt to guess login credentials through repeated login attempts. Due to these security concerns, many WordPress site owners choose to disable or limit XML-RPC access as a precautionary measure.
In recent years, the focus in WordPress development has shifted towards the REST API (Representational State Transfer Application Programming Interface) as a more modern and efficient alternative to XML-RPC. The REST API provides a standardized way to interact with WordPress, using the HTTP protocol and JSON (JavaScript Object Notation) format.
While XML-RPC still exists and can be useful in certain scenarios, it is important to consider the security implications and evaluate alternative options such as the REST API for remote communication in WordPress.
What are the security risks of not disabling XML-RPC in WordPress website?
Not disabling XML-RPC on a WordPress website can potentially expose it to several security risks. Here are some of the common security concerns associated with XML-RPC:
- Brute-force attacks: XML-RPC has been historically targeted by brute-force attacks, where hackers attempt to guess usernames and passwords by repeatedly making authentication requests through the XML-RPC interface. This can lead to unauthorized access to the website if weak or easily guessable credentials are used.
- DDoS attacks: XML-RPC can be exploited to launch Distributed Denial of Service (DDoS) attacks. Attackers can use the system.multicall method provided by XML-RPC to send a large number of requests, overwhelming server resources and causing the website to become slow or unavailable.
- User enumeration: XML-RPC can be abused to enumerate valid usernames on a WordPress website. Attackers can use the system.listMethods method to retrieve a list of available methods and then use the system.methodSignature method to determine if specific usernames exist on the targeted website.
- Content scraping: XML-RPC functionality provided by xmlrpc.php can be misused to scrape content from a WordPress website. Attackers can use the metaWeblog.getRecentPosts or wp.getPosts methods to retrieve post content, including sensitive information that should not be publicly accessible.
- Remote code execution: In some cases, vulnerabilities in XML-RPC itself or in plugins/themes that interact with XML-RPC can be exploited to execute arbitrary code on the server, leading to a full compromise of the website.
It’s important to note that not all websites are equally vulnerable, and the risks associated with XML-RPC can vary depending on the website’s configuration, installed plugins, and overall security posture. However, disabling XML-RPC can mitigate or eliminate these specific security risks associated with XML-RPC functionality.
As always, it’s recommended to implement a holistic security approach for your WordPress website, which includes regular updates, strong passwords, secure hosting, and additional security measures such as firewalls and security plugins, regardless of whether you choose to disable XML-RPC or not.
Should I disable XML-RPC in WordPress website?
Whether to disable XML-RPC in WordPress website depends on your specific security needs and the functionality you require. Here are a few considerations to help you make an informed decision:
- Security: XML-RPC has been known to be a target for some types of attacks, such as brute-force attacks that attempt to guess usernames and passwords. If you are concerned about the security of your website and don’t require the functionality provided by XML-RPC, disabling XML-RPC can be a proactive measure to reduce the attack surface.
- Functionality: XML-RPC enables certain features in WordPress, such as remote publishing from desktop applications or mobile apps. If you rely on these features or use third-party services that require XML-RPC access, disabling XML-RPC may limit or break their functionality. In such cases, it’s important to assess the impact on your workflows before making a decision.
- Alternatives: If you want to restrict access to XML-RPC but still require certain functionalities, you can explore alternative methods. For example, you can use plugins or security measures to limit or control access to XML-RPC, such as IP whitelisting or implementing a security plugin that provides granular control over XML-RPC capabilities.
- Up-to-date WordPress Version: Keeping your WordPress installation updated with the latest version is crucial for security. WordPress has made efforts to address security vulnerabilities associated with XML-RPC in newer versions. By ensuring your website is running on the latest version, you can benefit from the security improvements and fixes provided by WordPress.
Ultimately, the decision to disable XML-RPC should be based on your specific security requirements and the functionality you need. If you are uncertain or unfamiliar with the technical aspects, consulting with a WordPress developer or security professional can provide you with more personalized advice based on your website’s setup and needs.
How to check XML-RPC in WordPress website is enabled?
Start by verifying if XML-RPC in WordPress website is enabled or not. XML-RPC in WordPress is usually enabled by default, but some security plugins or server configurations may disable it. To check the status, follow these steps:
- Open a web browser (e.g., Chrome, Firefox, Safari).
- In the address bar, enter the following URL:
https://www.mydomain.com/xmlrpc.php. Replace “www.mydomain.com” with your actual domain name. As shown below in the image. - Press Enter or Return to load the URL.
- If you see a response or a blank page without any error messages, it indicates that XML-RPC is enabled and accessible on your website.
- If you receive an error message like “404 Not Found” or “Forbidden,” it suggests that XML-RPC is either disabled or restricted on your website.
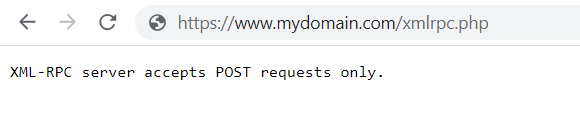
Note: If you have security plugins or server configurations that block direct access to XML-RPC, you may not see a response or encounter an error even if XML-RPC is enabled.
In such cases, you can use an online XML-RPC checker tool. These tools allow you to enter your website URL and check if XML-RPC is enabled or disabled. Simply search for “XML-RPC checker tool” in a search engine, and you will find various online tools that can help you with this.
How to disabled XML-RPC in WordPress?
To disable XML-RPC in WordPress, you have a few options depending on your specific needs and technical capabilities. Here are two common methods:
Method #1: Using a Security Plugin:

- Install and activate a security plugin that provides XML-RPC disable or control features. One popular plugin for this purpose is “Disable XML-RPC Pingback.“
- After installing the plugin, go to the plugin’s settings page (usually found in the WordPress dashboard under “Settings” or “Security”).
- Look for an option to disable XML-RPC or block XML-RPC requests and enable it.
- Save the settings, and the plugin will handle the XML-RPC disabling for you.
Method #2: Editing the .htaccess File:
- Connect to your website’s server using FTP or a file manager provided by your hosting provider.
- Locate the root directory of your WordPress installation, where the .htaccess file is located.
- Download a backup copy of the .htaccess file to your local computer as a precautionary measure.
- Open the .htaccess file using a text editor.
- Add the following code snippet at the beginning or end of the file:
# Disable XML-RPC
<Files xmlrpc.php>
Order Deny,Allow
Deny from all
</Files>Code language: HTML, XML (xml)- Save the changes and upload the modified .htaccess file back to the server, replacing the existing one.
By using either of these methods, you can effectively disable XML-RPC in WordPress. However, it’s important to note that some plugins or services may rely on XML-RPC for specific features or functionality. Therefore, before disabling XML-RPC in WordPress website, ensure that it doesn’t interfere with any essential functionality you may require or use on your website.
Additionally, keeping your WordPress installation, themes, and plugins up to date is crucial for overall security, regardless of XML-RPC being disabled. Regular updates help patch vulnerabilities and ensure the latest security enhancements are applied to your website.
The Future of XML-RPC in WordPress?
The future of XML-RPC in WordPress is somewhat uncertain. While XML-RPC has been a longstanding feature in WordPress, its usage and relevance have diminished over time due to various factors, including security concerns and the availability of more modern alternatives.
Here are a few points regarding the future of XML-RPC in WordPress:
- Decreased Usage: The usage of XML-RPC has significantly declined in recent years, primarily due to security vulnerabilities associated with it. Many WordPress site owners choose to disable or limit access to XML-RPC as a security measure, which further reduces its usage.
- Emphasis on REST API: WordPress has been actively promoting and developing the REST API as a more modern and efficient alternative to XML-RPC. The REST API offers a standardized and flexible way to interact with WordPress, and it has become the recommended approach for remote communication and integration.
- Security Concerns: XML-RPC has been a common target for brute-force attacks and other security vulnerabilities. As a result, there is ongoing debate and discussion within the WordPress community about the future of XML-RPC and whether it should be maintained or deprecated due to these security risks.
- Plugin and Theme Support: Some plugins and themes may still rely on XML-RPC for specific functionalities or integrations. However, as the popularity of XML-RPC continues to decline, it’s expected that plugin and theme developers will shift towards utilizing more modern alternatives like the REST API.
Considering the above points, it’s likely that XML-RPC will continue to diminish in importance and usage within the WordPress ecosystem. The emphasis will be on promoting and enhancing the REST API and other modern alternatives to provide secure and efficient remote communication capabilities. However, it’s important to note that any specific plans or decisions regarding the future of XML-RPC in WordPress would be determined by the WordPress core development team and the broader community.
What are some alternatives for XML-RPC?
While XML-RPC has been a widely used protocol for remote communication in the past, there are alternatives available that offer similar functionalities. Here are a few alternatives to XML-RPC:
- REST API: The WordPress REST API provides a modern and robust alternative to XML-RPC. It allows you to interact with your WordPress site using the HTTP protocol and JSON format. The REST API offers a more flexible and efficient way to retrieve and manipulate data, create or update posts, manage users, and perform various other operations.
- GraphQL: GraphQL is another alternative that provides a flexible and efficient way to query and manipulate data. It allows you to define the specific data requirements you need and receive a tailored response, reducing over-fetching or under-fetching of data. GraphQL offers a more streamlined and optimized approach compared to XML-RPC.
- Custom APIs: Depending on your specific requirements, you can develop custom APIs tailored to your needs. These APIs can be designed using any programming language and communication protocol of your choice, such as JSON-RPC or SOAP. Custom APIs provide the flexibility to define the functionalities and endpoints that align with your application’s requirements.
- Webhooks: Instead of relying on a remote communication protocol, you can implement webhooks to receive real-time notifications and data updates from external systems. Webhooks enable event-driven communication, where your WordPress site can react to specific events triggered by external services, applications, or platforms.
- Plugin-Specific APIs: Many plugins and services provide their own APIs or integration options to interact with WordPress. These APIs are tailored to specific functionalities and offer more specialized features. For example, popular e-commerce plugins often provide APIs for managing products, orders, and customer data.
When considering alternatives to XML-RPC, it’s important to evaluate your specific requirements, security considerations, and the availability of supporting libraries, tools, or plugins. The REST API is widely supported and recommended as a modern replacement for XML-RPC in WordPress, offering a robust and standardized way to interact with your site.
Frequently Asked Questions and Answers about XML-RPC in WordPress
-
What is XML-RPC in WordPress?
-
Is XML-RPC enabled by default in WordPress?
-
What are the security risks associated with XML-RPC in WordPress?
-
Are there alternatives to XML-RPC in WordPress?
-
Can I still use XML-RPC if I disable it in WordPress?
-
Can XML-RPC be used for mobile app integration with WordPress?
-
Does the WordPress REST API replace XML-RPC?
Role of Trailing Slashes in WordPress Permalinks
Curious about the role of trailing slashes in WordPress permalinks? Whether you’re a WordPress enthusiast, a developer, or a curious mind, this post is a must-read to explore the significance of trailing slashes, understand how they affect your website’s URLs. Click the link below to check out our blog post on “Role of Trailing Slashes in WordPress Permalinks”.
Conclusion
In conclusion, XML-RPC has played a significant role in the history of WordPress as a communication protocol, enabling remote interactions with WordPress sites. However, its relevance and usage have diminished over time with the emergence of newer and more modern alternatives like REST API.
While XML-RPC still exists in WordPress, its usage has declined due to various reasons. The protocol has faced security concerns, as it has been targeted by attackers and known vulnerabilities have been exploited. Additionally, the XML-based nature of the protocol introduces complexity and overhead, which can impact performance.
WordPress itself has been actively shifting its focus towards the REST API, which offers a more flexible and standardized approach to communication between systems. The REST API provides a robust and efficient means of integrating WordPress with other platforms, building custom applications, and retrieving and manipulating data in a structured manner.
Considering the pros and cons, it’s advisable to carefully evaluate the need for XML-RPC in your WordPress site. If your site doesn’t require XML-RPC functionality, disabling it can enhance security and reduce the attack surface. However, if you have specific plugins or legacy systems relying on XML-RPC, it may be necessary to maintain support for it, while implementing appropriate security measures.
It’s important to stay informed about the evolving WordPress ecosystem and security landscape. Keep your WordPress installation, themes, and plugins up to date, follow best security practices, and consider utilizing modern alternatives like the REST API to leverage the latest advancements in web communication.
Ultimately, the decision regarding the usage of XML-RPC depends on your specific requirements, security considerations, and the compatibility of your existing ecosystem. As WordPress continues to evolve, embracing newer technologies and protocols can help ensure the security, performance, and extensibility of your WordPress site.
Thank you for taking the time to read this blog post! If you found it helpful and informative, I would greatly appreciate your support in sharing it with your friends and colleagues. Your support helps me reach a wider audience and continue creating valuable content.
Feel free to share this post on social media, through email, or any other channels you prefer. If you have any comments, questions, or feedback, please don’t hesitate to leave them below. I value your input and look forward to engaging with you.
Thank you again for your support, and I hope to provide you with more insightful content in the future.





